Partner Device Verification
1. BACKGROUND
On Android tablets, the ZRC Play Store build contains logic to prevent its use on rooted devices, but for most partner devices, the root detection doesn't work. The partner build variant has root detection disabled, which causes a security gap on partner build variants. We want a digital signature verification method on partner devices to block the partner build variants use on unauthenticated devices. This document describes the details of the verification implementation.
2. OVERALL ARCHITECTURE
2.1 Preconditions
This method assumes that the partner can protect user data. It should be the partners' responsibility to make sure that the data on their device will not be leaked. Also, the device should have passed PAL authentication.
2.2 Certificates
Device-type-specific certificate: provided by partners, bundled in Zoom apps, and issued by a partner-specific CA.
Device-specific certificate: issued by the device-type-specific certificate, some partners want one certificate per device, to avoid one device's certificate leak affecting others.
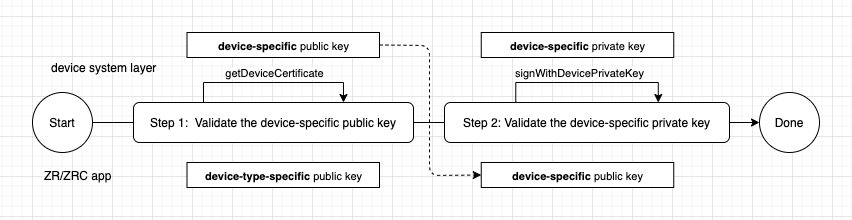
2.3 Verification Flow
Validate the device-specific certificate
- Zoom app gets the device-specific certificate by
ISystemManager.getDeviceCertificate. - Zoom app validates the certificate chain with bundled device-type-specific certificate.
- If true, continue to run, otherwise prompt a warning and automatically clean the user data and block the user.
- Zoom app gets the device-specific certificate by
Validate the device-specific private key
- Zoom app calls
ISystemManager.signWithDevicePrivateKeyAPI to sign a random code. - Validate the signature with a device-specific certificate.
- If true, continue to run, otherwise prompt a warning and automatically clean the user data and block the user.
- Zoom app calls
2.3 Vendor OS API
public interface ISystemManager {
/**
* Return the device specific public key, ZR will validate it with the bundled partner key.
* Require the capability of {@link SystemCapability#ZRAPI_SYSTEM_CAP_DEVICE_VERIFICATION}.
* @return PEM format device specific public key
*/
String getDeviceCertificate();
/**
* Sign the code with device's private key (<b>algorithm "SHA256withRSA"</b>), used by ZRC for verify the device is partners'.
* Require the capability of {@link SystemCapability#ZRAPI_SYSTEM_CAP_DEVICE_VERIFICATION}.
* @param codeToSign The random code to sign
* @return signed code with the the device specific key
*/
String signWithDevicePrivateKey(String codeToSign);
}
